
Cyber Threat Analysis Monitoring Ppt Powerpoint Presentation Styles File Formats Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

From Monitoring, Logging, and Network Analysis to Threat Intelligence Extraction | Taylor & Francis Group





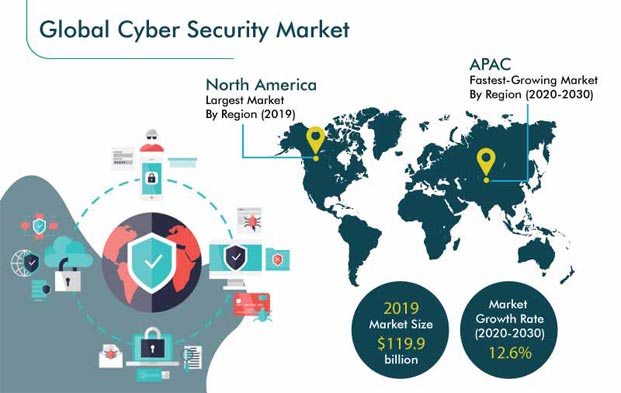
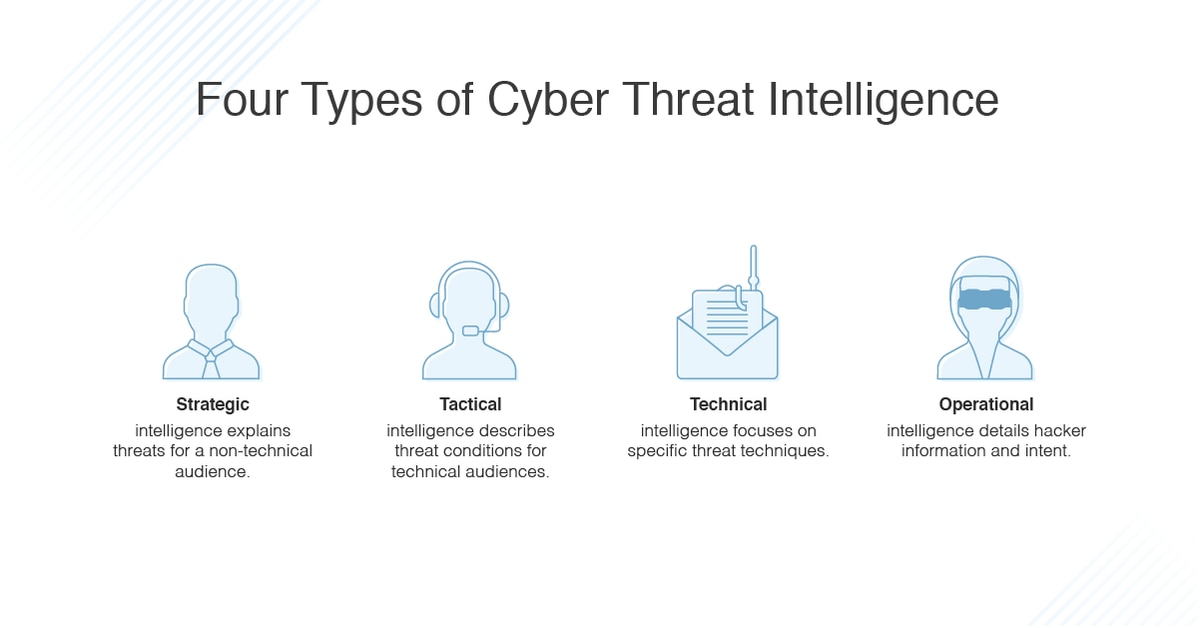

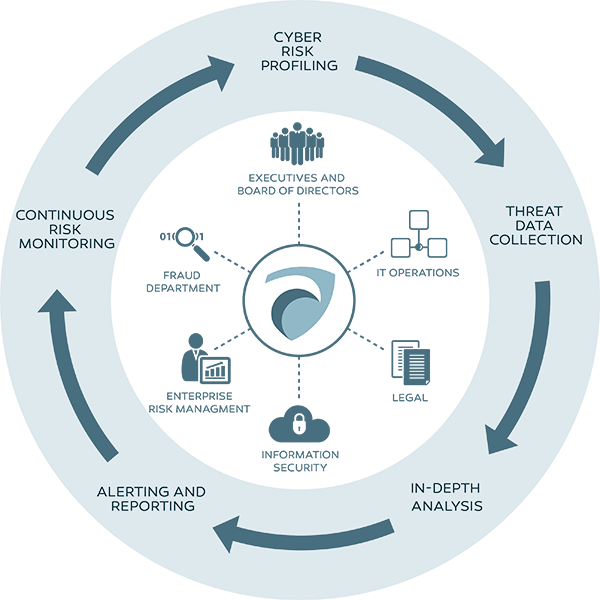


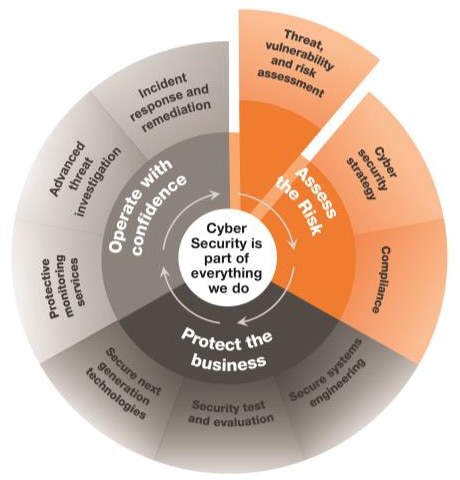
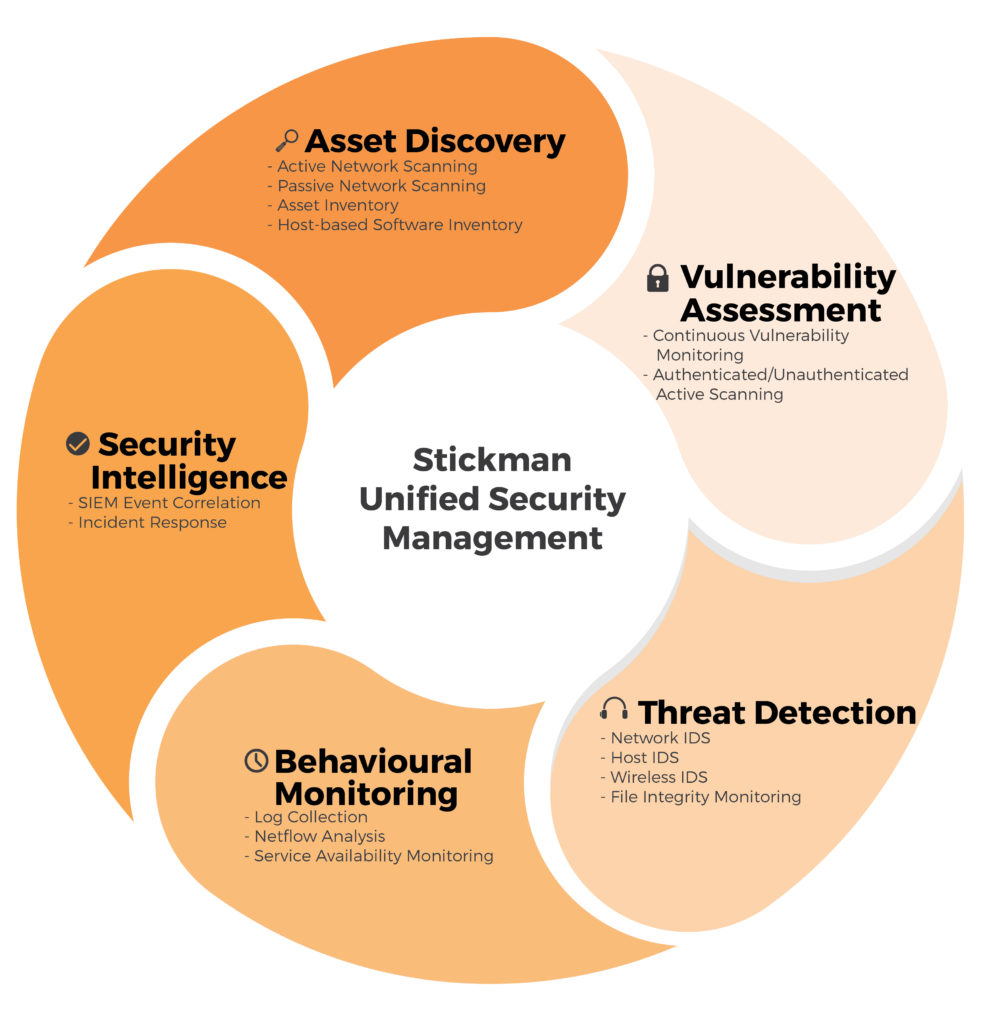
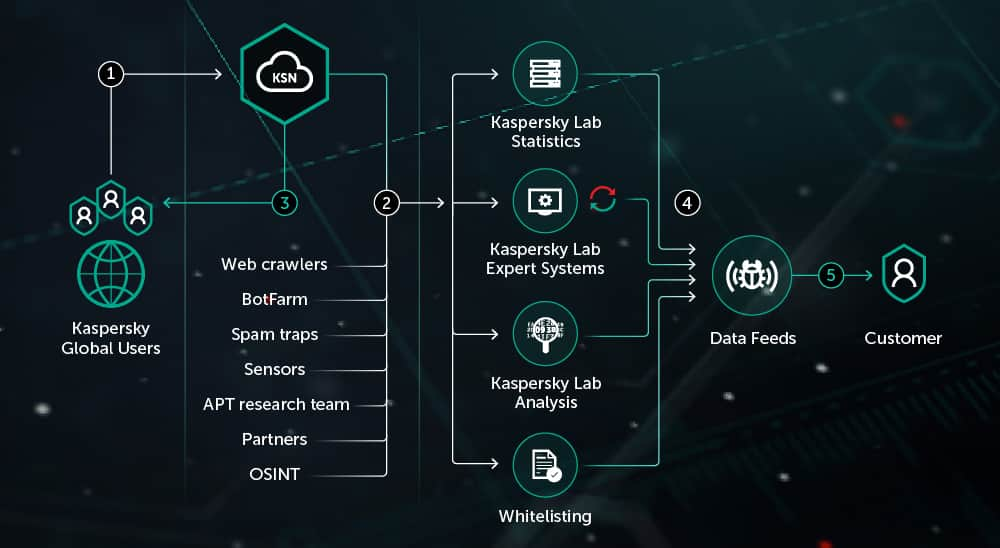


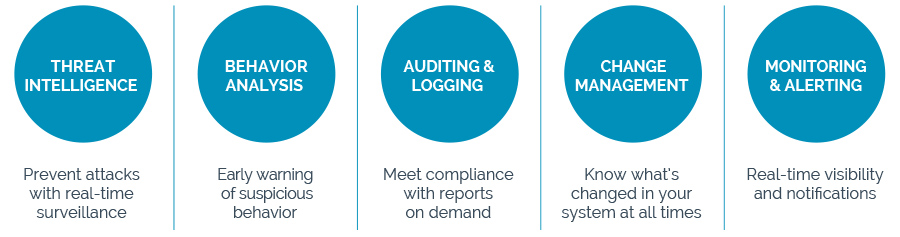

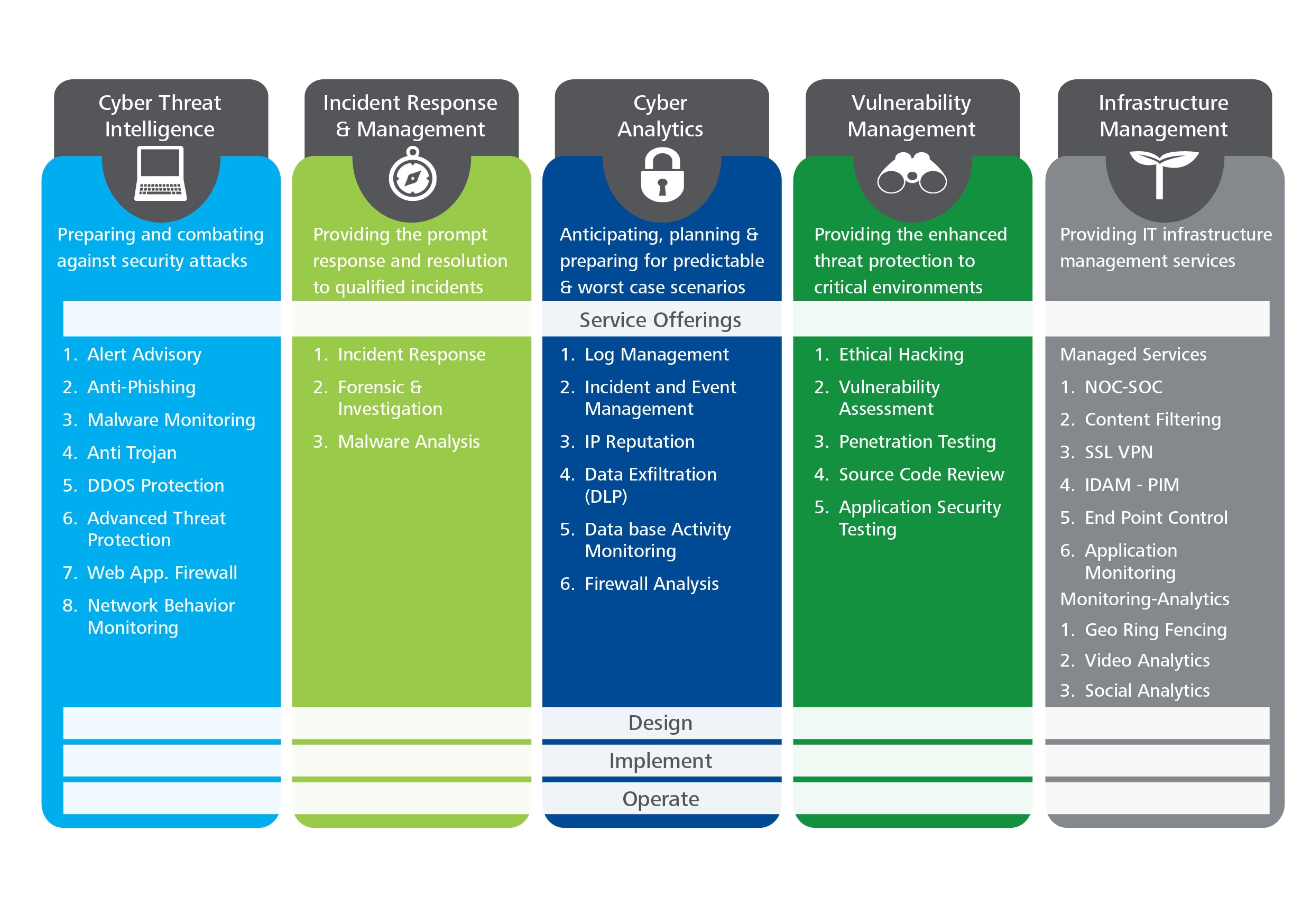



![What is Cyber Threat Intelligence? [Beginner's Guide] What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/crowdstrike-threat-intelligence-areas.png)